Why Desktop-as-a-Service (DaaS)
Shorter time to value
DaaS gets you onboard from the word go as compared to traditional VDI deployments that can take weeks or months.

Reduce burden on your IT teams
Managing VDI envrionment can be overwhelming for IT teams because of the sheer number of technologies and stakeholders involved in the service. DaaS, on the other hand, provides a single point of contact for the complete service.

Greater Agility & Resilience
Whether it is scaling up, scaling down or scaling out, DaaS provides agility to meet your changing business demands. Open new branch offices, onboard new vendors anywhere without much infrastructure investments.

Reduced TCO of your VDI service
With DaaS, you only pay for what you consume whereas on-premise deployments lock your investments from day 1 of service go-live irrespective of your utilization levels.
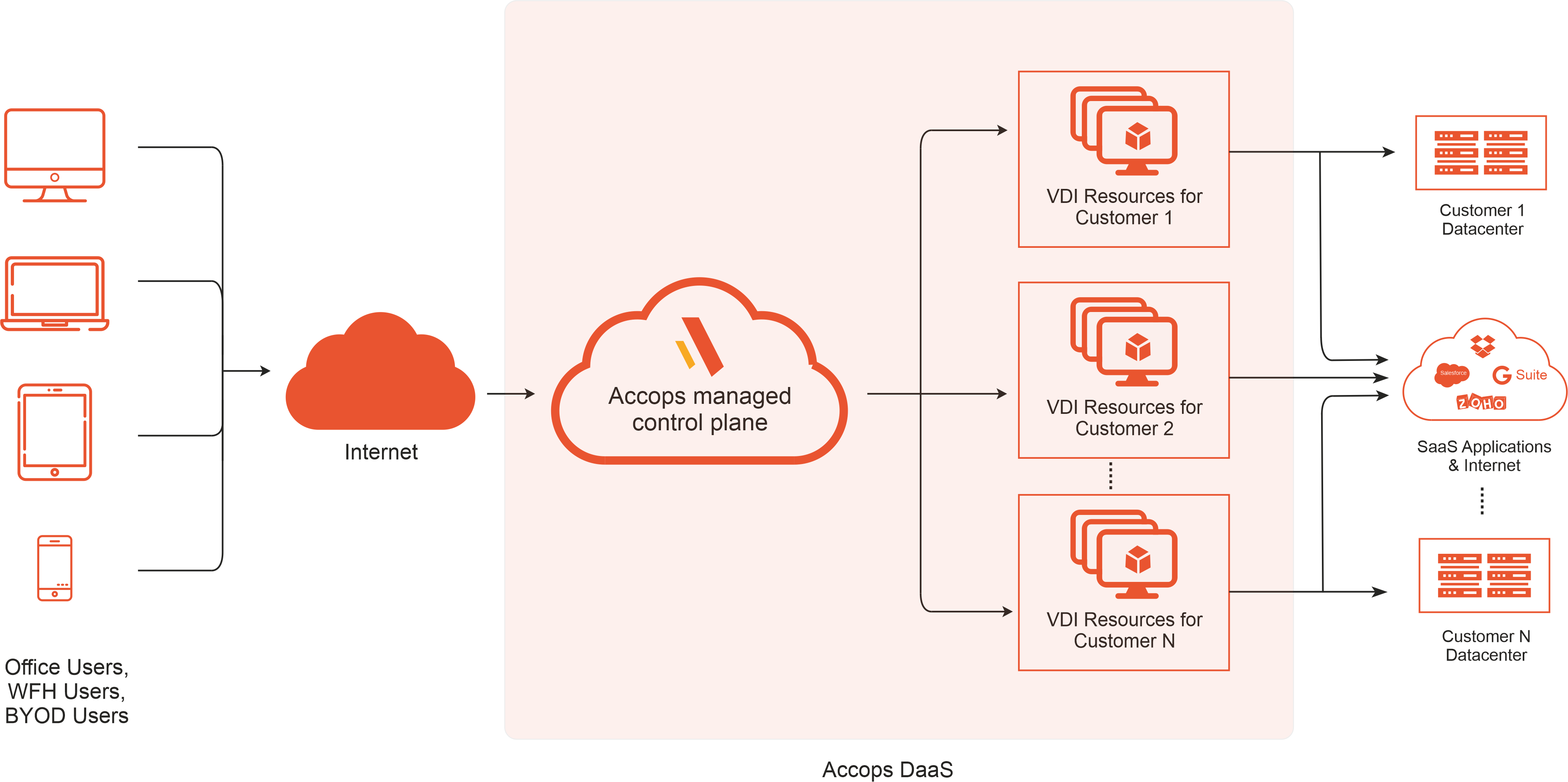
Why Accops DaaS

Completely managed services
Accops offering eliminates the complexity associated with managing virtual desktops completely. Professional services for managing the VDI environment are a part of the solution offered.

Unmatched security customizations
Based on the user role and criticality of the data involved, security features and policies can be customized. Contextual access can be enabled to evaluate each access request based on parameters like a user's role, device used, geolocation, time etc. before granting permissions.
Cost optimization by design
The solution is built to inherently optimize costs. Depending upon your requirements, enable access to private applications through either access gateway or DaaS.

Flexible provisioning models to suit your needs
Depending upon the level of control and customizations required by your IT, we provide you the flexibility to choose the topology and design that suits your specific needs.
Use Cases

- Work from AnywhereAccops provides organizations looking for a highly flexible and easily scalable IT infrastructure with an instant solution that addresses all security and management concerns associated with typical remote work solutions.
- Seamless Business ContinuityKeep your critical functions up and running by quickly enabling secure access to business applications from anywhere, even during global pandemics or local calamities.
- Fast onboarding of vendors, developersInstantly provision secure workspaces for new employees as well as vendors, developers, and consultants. Seamlessly revoke access once a vendor's contract period is over.
Features
Pooled and personal desktops
Catalogue of pooled and personal desktops with a choice of Windows 10, Windows Server OS or Linux OS depending upon your users' needs.
Contextual access
Provide Zero trust-based access with contextual policies, and grant or deny access, or enforce further authentication, depending upon on the context of requests.
Data protection control
The endpoint control features enable you to protect the environment from unauthorized access and control user activities like data copy/paste and downloading, screen printing, screen sharing, etc., to prevent data leakage.
Multi-factor authentication
Robust multi-factor authentication capability that supports SMS, Email, Mobile app and even biometric evidence (face and finger print) adds a strong layer of security.
Deep integration with Azure
Integration of our control plane with Azure provides a GUI thus simplifying management activities on the cloud. Additionally, the solution also supports all Azure features like Windows 10 Multi-session, FSLogix app attach, Audio Video optimization of MS Teams et al.
Reduce costs through efficient power management of VMs
With power management options along with the idle timeout feature that are natively available from the Accops platform, you can optimize your virtual desktops utilization based on usage patterns and user activity, and save costs.
Integrated thin client provisioning and management
Energy efficient, cost effective & ergonomic Accops thin clients can be provisioned and managed centrally from the Accops DaaS console without the need of any third party products.

Empower BYOD users
Enable business users to work from any device of their choice - personal laptops, desktops or smartphones. Accops Nano, a customized and hardened Linux based live operating system, which is free from any keylogger or malware can be provisioned for BYOD users.
Zero capex
A true pay-as-you-go model that gives you enterprise grade virtual workspaces with just the monthly subscription fee.
Customer Stories
Trending Topics
The case study has been sent to your mail ID.
Your details have been shared with Accops.








